In the light of today’s threat landscape, the importance of data security and ensuring our data is safe is now the concern of each individual both personally and professionally. Let’s get discussing about how Zero Trust has become a worldwide tech trend these days.
Since the information of an individual or organizations that are confidential in nature must be beyond the knowledge, reach or manipulation of any external entity, the concept of implementing perimeters arose.
We tend to trust the intermediate segments, and we do not know if the data being transacted is safe, secure, or untampered.
Convergence of technology with communication & business has been outpacing the legal protection afforded to an organization’s security.
Since the universal distribution across all nations without barriers of sovereign controls, securing cyberspace is by no means an easy task. The US government while implementing its National Strategy to Secure Cyberspace states that „cyberspace is itself chaotic in nature and beyond the reach of any organized or central body “. Thus, concepts like IT Acts, cyber laws, cyber security, zero trust, anonymity networking, data privacy, data protection have been brimming up.
Zero Trust: Concept
„Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. It assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.“
This newly emerged architecture ensures hygiene in cyberspace. It primarily focuses on user, data and assets involved inside the network which is a strategy traditionally considered trusted or safe. Zero Trust (ZT) says to not trust any form of network perimeter / barriers commonly used, say for example firewalls nor any individual trying to access data.
The idea of ZT was initially brought to life by a group called Jericho Forum back in 2004, However John Kindervag re-coined the term „Zero Trust“ in 2010.
This architecture supports organizations that are transitioning to Software defined network or SD-WAN, Cloud Usage and forms of Hybrid Workforce. ZT provides us the ability to divide the existing perimeter to go almost perimeter-less in a granular point of view, isolate and control the workflow.
The Key Components of Zero Trust:
- Users – Authenticate at every request from any location of every user
- Devices – Validate every device for its trustworthiness
- Network – Monitor the network at each perimeter and hub to isolate critical data
- Applications – Validating the requestor and its access privilege
- Automation – Integrate workflows and security automation in a unified manner
- Analytics – Tools to enable transparency of every emerging threats / events
Illustration of the difference between a traditional, firewalled network, with zero-trust architecture by A.Kerman/NIST.
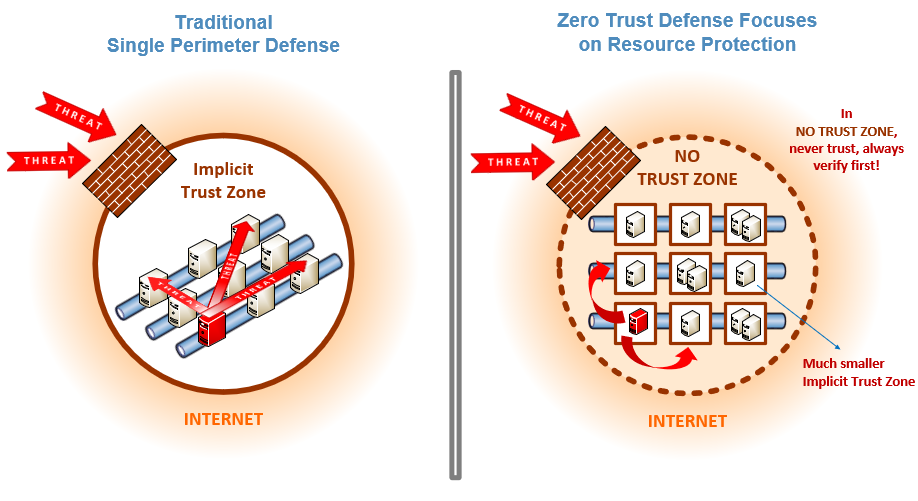
We communicate and digest resources and information from all types of cloud variations for the reason why a huge footprint of services and applications are needed to be accessible from anywhere. The risk in this form of exchange has directly been increased, all the while simplifying security management and resilience.
In an annual survey conducted by Okta recently, it seems that 72% of government entities are already implementing Zero Trust strategies in their networks. Although the security posture is taking more attention these days, many industries already employ ZT in their infrastructure.
Come join us in this run for securing your organization. Zero Trust Solutions and consulting by mispa put out a comprehensive range of services for you to choose from. This enables high business agility in a secure and controlled way.
As a digital enterprise, you will want to push significant changes onto your IT teams.
mispa, is providing world’s leading security technology solutions and a global team of experts.
mispa, is providing world’s leading security technology solutions and a global team of experts. We at mispa are making sustainable use of digital opportunities with risk based IT-security. We believe in technology for a safer infrastructure, and are here to support you.
